
What is Ethical Hacking?
An authorized attempt to acquire unauthorized access to a computer system, application, or data is known as ethical hacking. Duplicating the techniques and behaviors of malevolent attackers is part of an ethical hack.
This approach aids in the detection of security flaws, which can subsequently be addressed before a malevolent attacker can exploit them.
What is an ethical hacker?
Ethical hackers, commonly known as “white hats,” are protection specialists who conduct these audits. They assist an organization’s security posture by being proactive.
The objective of ethical hacking differs from criminal hacking in that it requires prior clearance from the corporation or owner of the IT asset.
What are the key concepts of ethical hacking?

Hackers adhere to four important protocol principles:
- Stay legal
Before obtaining and completing a security assessment, get proper approval.
- Define the scope
Determine the scope of the assessment to ensure that the ethical hacker’s work is legal and within the organization’s allowed parameters.
- Report vulnerabilities
All vulnerabilities identified during the evaluation should indeed be communicated to the organization. Offer suggestions for fixing these issues.
- Respect data sensitivity
Ethical hackers may be forced to sign a non-disclosure agreement in addition to additional terms and restrictions imposed by the examined organization, depending on the sensitivity of the material.
How are ethical hackers different than malicious hackers?
Ethical hackers employ their skills to help corporations secure and improve their systems. They perform an important benefit to all of these companies by checking for security vulnerabilities that could lead to a data leak.
The found vulnerabilities are submitted to the organization by an ethical hacker. They also offer remedial suggestions.
In many instances, the ethical hacker conducts a re-test with the organization’s permission to assure that the vulnerabilities have been thoroughly addressed.
For financial benefit or personal notoriety, malicious hackers seek unauthorized access to the information. For pleasure, reputation damage, or financial gain, some malicious hackers deface websites or crash backend servers.
The methods employed and vulnerabilities discovered are yet unknown. They are unconcerned with the security posture of the organization.
Importance of Ethical Hacking
Terrorist organizations employ hackers to breach security systems in the early stages of international wars, either to damage national security features or to extort considerable amounts of money by introducing malware and withholding access.
As a result, cybercrime is already on the rise. Before falling prey to a hacker, organizations must update their hack-prevention strategies and deploy different technologies to defend the system.
Every day, new worms, malware, viruses, and ransomware are released, requiring the usage of ethical hacking operations to protect the networks of corporations, government entities, and defense.
What skills and certifications should an ethical hacker obtain?
An ethical hacker must be well in a variety of computer technologies. They frequently specialize, in acquiring subject matter experts (SME) in a certain field of ethical hacking.

The following are some of the most well-known and achieved certifications:
- Certified Ethical Hacking Certification from the EC Council
- Certification as an Offensive Security Certified Professional (OSCP)
- CompTIA Security+ certification
- Cisco’s CCNA Security SANS GIAC certification
Benefits of Ethical Hacking
The fundamental benefit of ethical hacking is that it prevents malevolent attackers from stealing and misusing data, as well as:
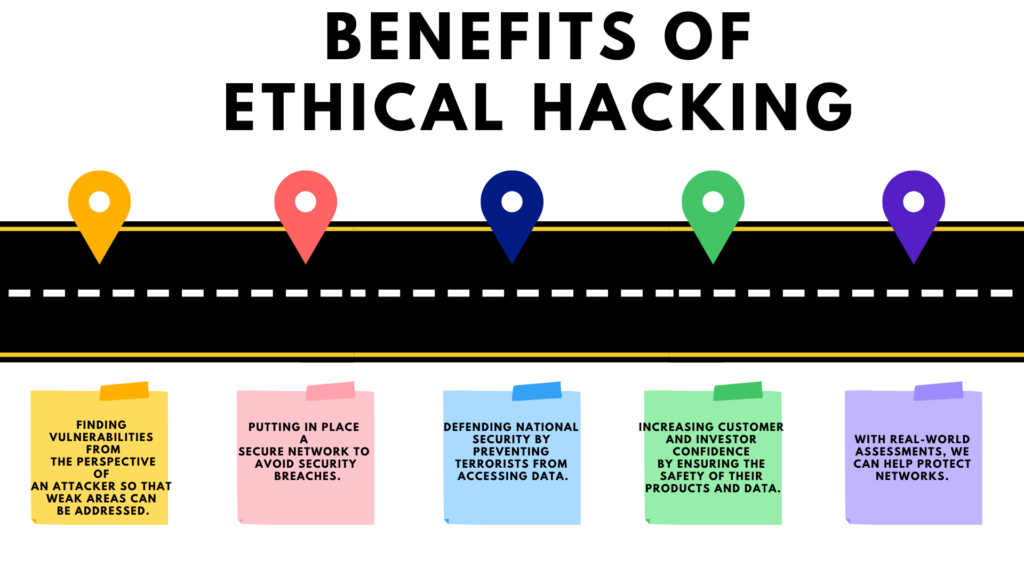
What problems does hacking identify?
Ethical hacking attempts to emulate an attacker while examining the protection of an organization’s IT assets. They are looking for threat vectors against the victim while doing so. The first objective is to conduct an investigation and gather information as possible.
Again when the ethical hacker has gathered enough knowledge, they examine the asset for weaknesses. They use a mixture of automated and manual testing to complete this assessment. Even sophisticated capabilities may be vulnerable to complex countermeasure methods.
They don’t just look for flaws. Exploits have been used by ethical hackers to demonstrate how a pernicious attacker might exploit a vulnerability.
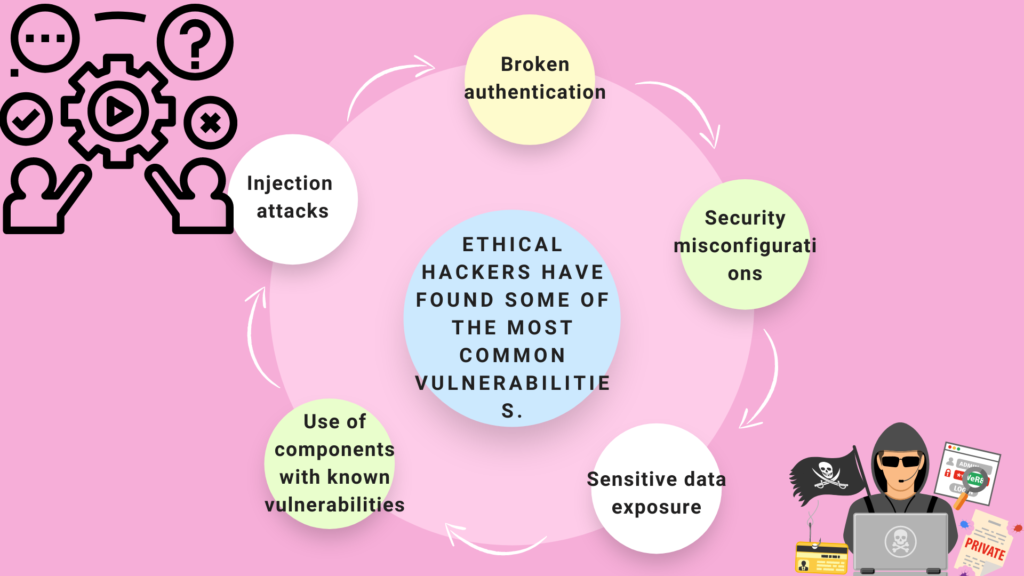
Ethical hackers provide a full report following the testing period. This literature offers instructions on how to exploit the disclosed flaws as well as how to patch or mitigate them.
Read Also: What is Hacking And Different Types of Hackers
Types of Ethical Hacking
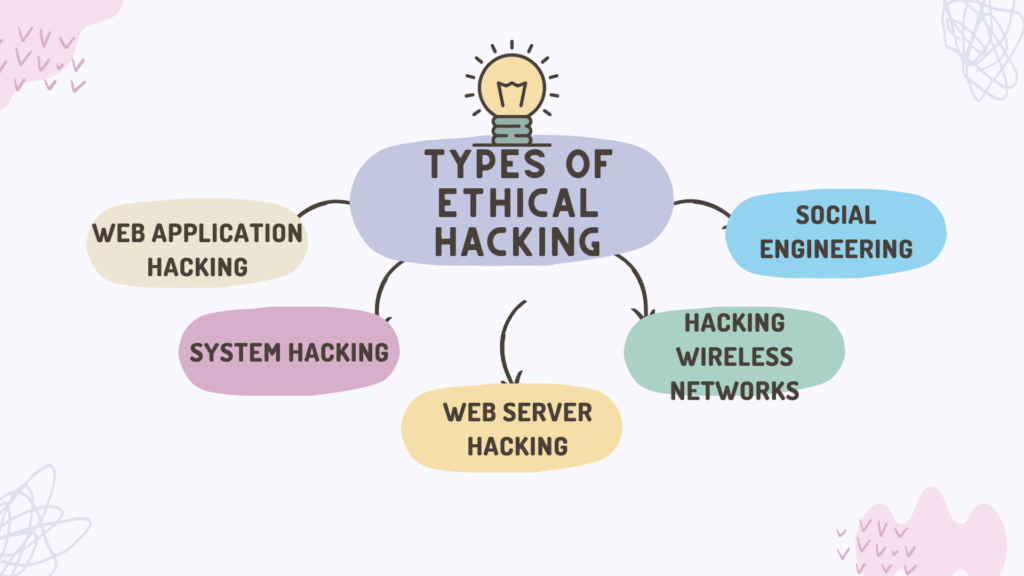
- Web Application hacking
Web hacking is the process of attacking software over HTTP by making use of the software’s visual Chrome browser, tampering with the URI, or cooperating with HTTP elements not stored in the URI.
- System Hacking
Hacktivists use system hacking to obtain access to personal computers on a network. IT security specialists can use password busting, privilege escalation, malicious software development, and packet sniffing as defensive techniques to resist these threats.
- Web Server Hacking
Real-time web information is generated by a software applications database server. To steal credentials, passcodes, and information about the company from the online application, attackers use gluing, ping deluge, port scan, sniffing assaults, and social engineering tactics.
- Hacking Wireless networks
Although wireless networks communicate via radio waves, an attacker can easily attack the network from any nearby location. These assailants frequently utilize network sniffing to discover the Identifier and patch it up on a wireless network.
- Social Engineering
Social engineering is the technique of influencing the public into divulging critical information. Criminals utilize eugenics because it is easier to target your natural inability to trust than it is to figure out how to spoof your device.
Phases of Ethical Hacking
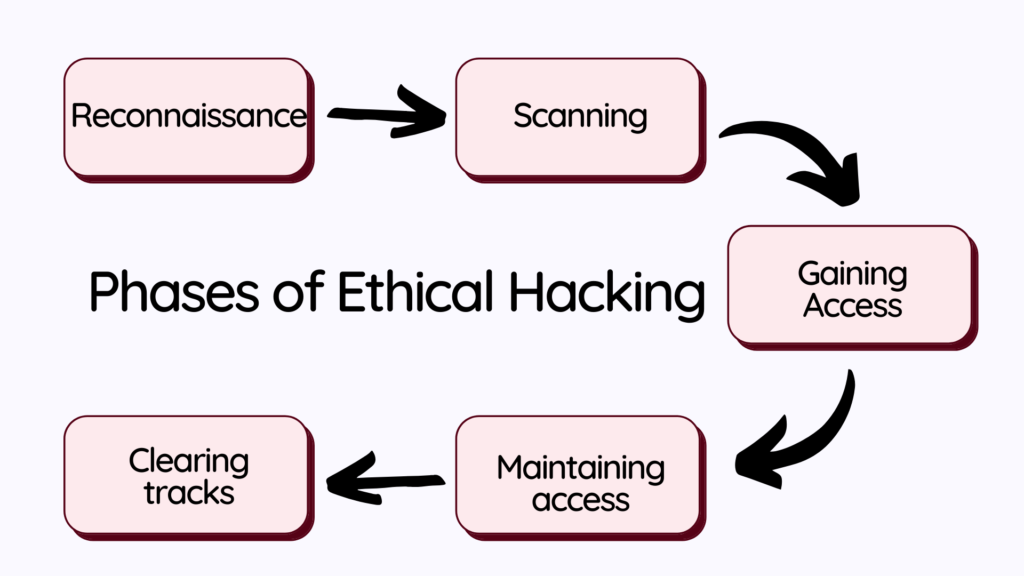
- Reconnaissance
You should obtain some preliminary knowledge about the target system before attempting any attack. This information could include details about the target’s people or organizations, the host system, or the target network. The main aim of this process is to create a hack using the precise security and management mechanisms used by the target computer.
- Scanning
Hacking is usually accomplished through network access. Almost all of our devices are connected to the system, even if they are in an office or at home. Wi-Fi or WLAN is the most widespread type of network. Ethernet connections are indeed installed in offices to ensure optimal efficiency.
As a hacker, you can use this to your advantage and concentrate on gaining illegal access to the target host’s network. The network topology and vulnerable interfaces are discovered throughout this procedure.
- Gaining Access
The information collection phase has been completed with the two stages listed above. You must now begin your hack based on this knowledge. This stage entails cracking the targeted system’s password or circumventing the security mechanisms.
- Maintaining Access
After acquiring access, you must guarantee that you can retain access to the target system until your first session is completed. This is accomplished via a backdoor. Backdoors are exploits or hacks that are left in the target system to allow future access. If you don’t leave a backdoor, the target system may apply a newer security patch or reset its security measures, forcing you to repeat the hacking process.
- Clearing Tracks
It’s critical to clean up the aftermath of your attack or hack when you’ve finished. This step includes removing any backdoors, executable code, or logs that could be used to track the attack back to you or discover it in the first place.
Roles and Responsibilities Of Ethical Hacker
Let’s discuss the obligations of a Certified Ethical Hacker:
- Meeting with your customer to discuss the current security systems in place.
- Verifying the system, network topology, and susceptible access points of the organization.
- Performing system penetration testing (s).
- Security flaws and vulnerabilities must be identified and documented.
- The network’s security is being tested.
- Identifying the most effective security solutions.
- Reporting about penetration tests.
- Penetration testing is carried out after suggested or new security mechanisms have been implemented.
- Finding replacements for security features that aren’t working
What are some limitations of ethical hacking?
- Limited scope
To make an attack successful, ethical hackers cannot go beyond a defined scope. However, it’s not unreasonable to bring up the possibility of an out-of-scope attack on the organization.
- Resource constraints
Malicious hackers are not bound by the same time limitations that ethical hackers are. Ethical hackers face additional limits in terms of computing power and budget.
- Restricted methods
Some companies hire experts to help them avoid test scenarios that cause servers to fail (such as DoS assaults).
Conclusion
Ethical hacking is a difficult area to study because it requires an understanding of all aspects of a system or network. Certifications have grown popular amongst aspiring ethical hackers because of this. This article provides detailed what ethical hacking is or what the ethical hacker’s roles and obligations are.
Disclaimer
This Article is demonstrated for instructional purposes only. It is illegal to use it in the wrong way. We don’t approve of any type of hacking in any way. The end-users should be solely responsible for their own behaviors.
People May Ask
Q- What is the role of an ethical hacker?
A- An ethical hacker, also known as a white hat hacker, is a computer security specialist who breaks into a computer system, network, application, or another computing resource on behalf of its owners and with their permission.
Q- What is ethical hacking?
A- An authorized attempt to acquire unauthorized access to a computer system, application, or data is known as ethical hacking. Duplicating the techniques and behaviors of malevolent attackers is part of an ethical hack.
Q- Is hacking a profession?
A- If you’re looking for a stimulating and ever-changing work environment, ethical hacking is a terrific career choice. You desire a job that makes a difference. You wish to protect yourself against cyber-attacks.
Q- Is ethical hacking a simple task?
A- Penetration testing, intrusion testing, and red teaming are all terms used to describe ethical hacking. Getting a career as an ethical hacker isn’t easy; it takes a lot of knowledge, especially when it comes to computer system security and a lot of experience.
Q- What is the name of a good hacker?
A- White Hat Hackers.







