What Is Hacking? Are you concerned about being hacked? Have you had nightmares about cloaked hackers probing into your most personal information? If you’re worried about hacking, you’ve come to the right spot. Our complete hacking tutorial will answer all of your worries.
It’s realistic to assume that in the internet age, bad hackers will target all organizations and services at some point. That’s not a problem of if, and therefore when.
What is Hacking, Anyway?
The term “hacking” comes from a Germanic word that means “to cut in pieces.” It refers to the process of putting information (or anything else) together in a creative way to produce something interesting or valuable.
In the domain of computers, the term began with a positive connotation—Steve Wozniak, one of Apple’s initial creators, was a master hacker.
The term “hacker” is now more commonly used to indicate someone who finds and exploits a computer system flaw or vulnerability.
Hackers use flaws to obtain access to more computers in a network or to prevent system access. This isn’t to say that all hackers are “evil guys.” Penetration testing, for example, is an ethical hacking career.
Who is a Hacker?
A hacker is someone who seeks out and exploits flaws in computer systems and/or networks in order to gain access. Hackers are typically experienced computer programmers who are also knowledgeable about computer security.
Not All Hackers Are the Same
There are various types of hackers. Some of the most commonly used terms to characterize hackers and what they accomplish are:
Different Types of Hackers
In order to distinguish between the numerous types of hackers that exist in the cyber sector and their roles and objectives, it is necessary to understand the various types of hackers that exist in the cyber segment. The following are examples of hackers:
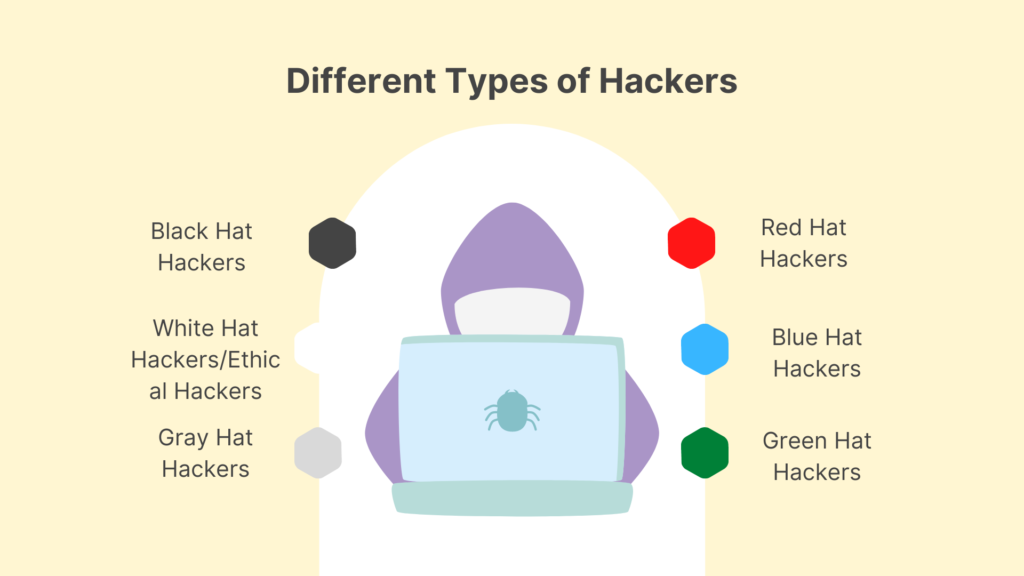
Black Hat Hackers
These hackers, also known as crackers, always have a malevolent intent and attempt to obtain unauthorized access to computer networks and websites.
They want to gain money by stealing confidential company information, stealing funds from online bank accounts, violating privacy rights to benefit criminal organizations, and so on. The bulk of hackers in today’s world fall into this category and operate in a shadowy manner.
Black hat hackers are unscrupulous persons who want to exploit and damage others by utilizing their technical expertise. They frequently have the skills and knowledge to get into computer networks without the owners’ permission, exploit security flaws, and bypass security safeguards.
They set out with the malicious intent of getting unauthorized access to networks and systems.
White Hat Hackers/Ethical Hackers
The polar opposites of black hat hackers are white hat hackers (also known as ethical hackers). They use their technical knowledge to protect the world from dangerous hackers.
Businesses and government agencies hire white hats as data security analysts, researchers, security professionals, and other roles. White hat hackers utilize the same hacking techniques as black hackers with the approval of the system owner and good intentions.
They can work for businesses as contractors, freelancers, or in-house employees. They help their customers fix security holes before criminal hackers can take advantage of them.
Gray Hat Hackers
They are a hybrid of the two categories of hackers in that they acquire unauthorized access to a system but do so without harmful intent.
The purpose is to reveal the system’s flaws. Grey hat hackers may offer to remedy vulnerabilities discovered by their own unauthorized activity rather than exploiting them for illegal gain. For example, they may penetrate your website or application without your consent in order to look for vulnerabilities. They almost never, if ever, attempt to harm others.
Grey hats do this to build a reputation and notoriety in the cyber security profession, which will help them advance their careers as security experts in the long term. On the other side, this action tarnishes the reputation of the companies whose security weaknesses or exploits are made public.
Red Hat Hackers
Also called “eagle-eyed hackers.” Red hat hackers aim to make it harder for threat actors to launch unethical attacks. Red hat hackers have the same goals as ethical hackers, but they use different tactics. Red hat hackers may use illegal or extreme methods. Threat actors’ systems are routinely targeted by red hat hackers.
Blue Hat Hackers
Blue hat hackers are security specialists who work outside of an enterprise. Companies routinely urge people to test new software and find security problems before releasing it. Blue hat hackers are periodically invited to help companies find holes in their important internet systems.
Some hackers aren’t concerned about money or celebrity. They hack to extract personal vengeance on someone, their company, their organization, or the government for a genuine — or imagined — deceit.
Blue hat hackers use malicious software and various cyber threats on their opponents’ devices to harm their data, websites, or devices.
Green Hat Hackers
Green hat hackers aren’t knowledgeable with internet security or internal dynamics, but they’re quick learners who are motivated (if not desperate) to rise in the hacking industry.
Although they are unlikely to intentionally harm others, they may do so while “testing” different infections and attack techniques.
As a result, green hat hackers can be harmful since they are often uninformed of the consequences of their actions – or, worse, how to rectify them.
What can Hackers do?
While your computer is connected to the Internet, spyware installed by a hacker sends your personal and financial information to third parties without your knowledge or consent. Hackers are able to:
- Usernames and passwords are stolen.
- Obtain a cash advance Steal your money and open credit cards and bank accounts in your name.
- Delete your credit history.
- Take use of your Social Security number.
- Create a new account with the request Personal identification numbers or additional credit cards (PINs).
- Personal information is misused and shared with third parties ( illegal purposes).
- Invest in something.
How to identify that your system is hacked?
If a hacker has gained access to your system, you will notice the following warning signs:
- Your computer, smartphone, or tablet begins to act strangely, such as the password no longer working, device settings changing, camera and microphone activation, and so on.
- Your system’s antivirus software is turned off without your knowledge.
- It is the most important component in protecting your system; if it is turned off without your knowledge, it is a clear indication that your system is under attack.
- Hackers usually divert your browser or internet traffic to a malicious website.
- Then it’s a clue that your system has been compromised.
- If someone takes money from your account without your knowledge.
- When a hacker gains access to your account, the first thing he or she does is change your account’s password.
- When your password no longer works, it signifies someone has changed your account password.
- Hacking also includes seeing suspicious adverts or popups on your computer on a regular basis.
Devices Most Vulnerable To Hacking
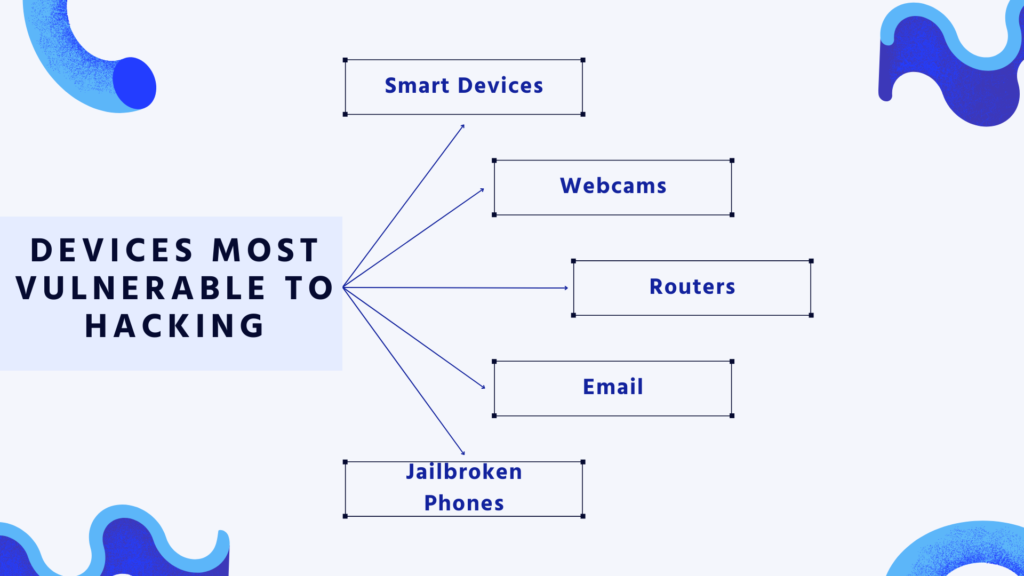
Smart Devices
Smartphones as well as other smart devices are vulnerable to hackers. Android devices, in particular, have a more open-source and uneven software development process than Apple devices, making them more vulnerable to data theft and corruption. However, hackers are increasingly targeting the Internet of Things’ millions of devices (IoT).
Webcams
Webcams incorporated into computers are a popular target for hackers, owing to the ease with which they may be hacked. Hackers generally acquire access to a computer with rootkit malware’s Remote Access Trojan (RAT), which allows them to read users’ communications, see their browser activities, take screenshots, and hijack their webcam.
Routers
An attacker can get access to data delivered and received via routers, as well as networks that are accessed through them, by hacking them. Hackers can also use a router to carry out larger-scale malicious activities like distributed denial-of-service (DDoS) assaults, DNS spoofing, or crypto mining.
Among the most typical targets of cyberattacks is emails. It’s used to transmit malware and ransomware, as well as phishing attacks, when attackers utilize harmful attachments or links to target victims.
Jailbroken Phones
Jailbreaking a phone entails eliminating restrictions placed on its operating system, allowing the user to install apps and other software not accessible through the phone’s official app store.
Jailbreaking exposes various vulnerabilities, in addition to being a violation of the end-license user’s agreement with the phone developer.
Hackers can target jailbroken phones, allowing them to not only steal any data stored on the device, but also to attack related networks and systems.
Common techniques used in hacking
How do hackers do what they do now that we’ve covered what they do? Depending on what the hacker is wanting and who they’re going after, they can use a variety of hacking techniques. Let’s look at some of the most typical hacking cases to learn more about the many sorts of computer hacking.
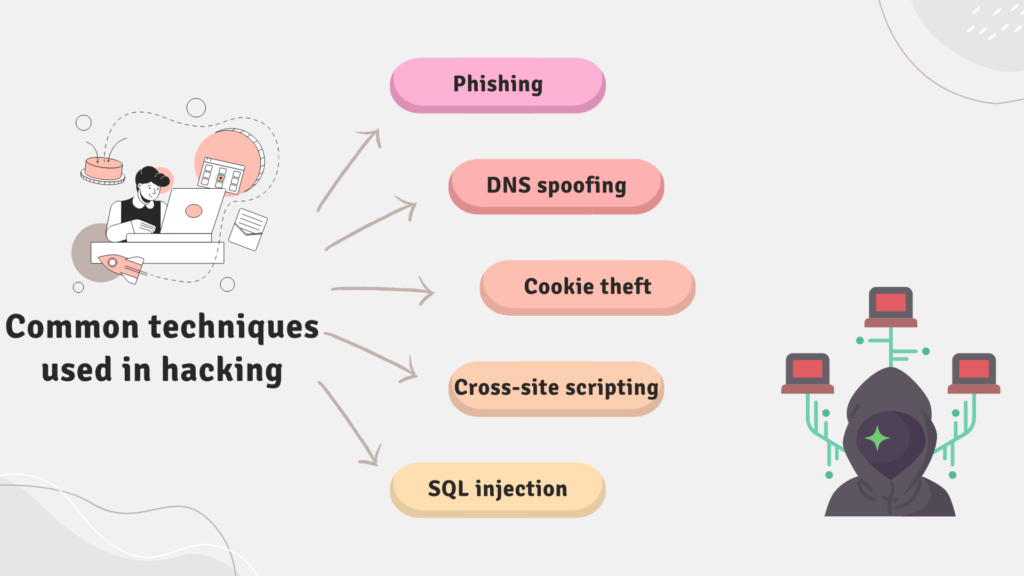
Phishing
Phishing is a devious type of cyber assault in which a cybercriminal tries to trick their victims into handing over sensitive personal information such as passwords or credit card numbers.
The attacker can then use that information to get access to a victim’s accounts and perpetrate fraud or theft, generally by making purchases or applying for loans with the victim’s identity.
DNS spoofing
DNS spoofing is a method of deceiving your browser into sending your internet traffic to an incorrect location. Websites and web servers can identify themselves online in two ways.
The first is the domain name, which is what you type into your browser’s address bar . The IP address is a string of digits that allows any device on the internet to identify any other device with which it is interacting.
Cookie theft
Cookie theft, also known as session hijacking, occurs when a hacker takes session data and uses it to impersonate you on a website. Cookies are little text files that websites save in your browser to remember your preferences, settings, and activity.
A session is a data exchange between you and a web server that lasts from the time you first visit a site until the time you leave or close your browser.
Cross-site scripting
Cross-site scripting (XSS) is a website attack in which a hacker inserts their own code into a genuine website. As a result, the website behaves differently, usually to the detriment of other users.
SQL injection
Another sort of attack is SQL injection, in which a hacker injects their own code into a website. SQL injection attacks, on the other hand, target the database stored on a website’s server rather than changing how it works.
The goal is to modify the database by copying, altering, deleting, or otherwise changing it. Cross-site scripting (XSS) is a website attack in which a hacker inserts their own code into a genuine website. As a result, the website behaves differently, usually to the detriment of other users.
Prevention from Getting Hacked
There are a few critical measures and best practices that organizations and people may follow to guarantee that they are less likely to be hacked.
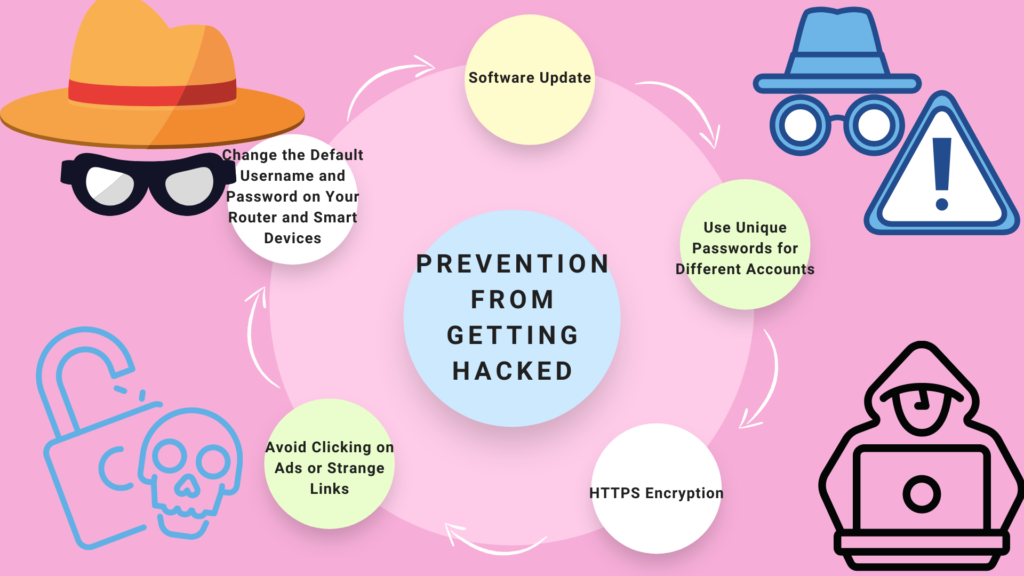
Software Update
Hackers are continually on the lookout for security flaws that have yet to be discovered or addressed.
As a result, keeping software and operating systems up to date is critical to keeping people and companies safe from hackers.
They must allow automatic updates and ensure that all of their devices and programs have the most recent software version installed.
Use Unique Passwords for Different Accounts
The most common source of data leaks and cyberattacks is weak passwords or account credentials, as well as improper password management.
Not only should you choose strong passwords that are difficult to crack, but you should never use the same password for multiple accounts. To restrict the efficacy of hackers, use unique passwords.
HTTPS Encryption
Another prevalent method of data theft is spoofing websites, in which hackers create a fake website that appears authentic but steals the credentials that users submit. At the beginning of a site address, look for the Hypertext Transfer Protocol Secure (HTTPS) prefix.
Avoid Clicking on Ads or Strange Links
Hackers frequently employ advertisements such as pop-up adverts. When they are clicked, they mistakenly download malware or spyware onto the user’s device. Strange links contained in email messages or on social media, in particular, should never be clicked. Hackers can use them to install malware on a device or redirect visitors to bogus websites.
Change the Default Username and Password on Your Router and Smart Devices
Default identities and passwords come with routers and smart devices. However, when suppliers ship millions of devices, the credentials may not be unique, increasing the possibility of hackers hacking into them. Setting a unique login and password combination for these types of devices is great practice.
Protect Yourself Against Hacking
Users and organizations can take further actions to protect themselves from the possibility of hacking.
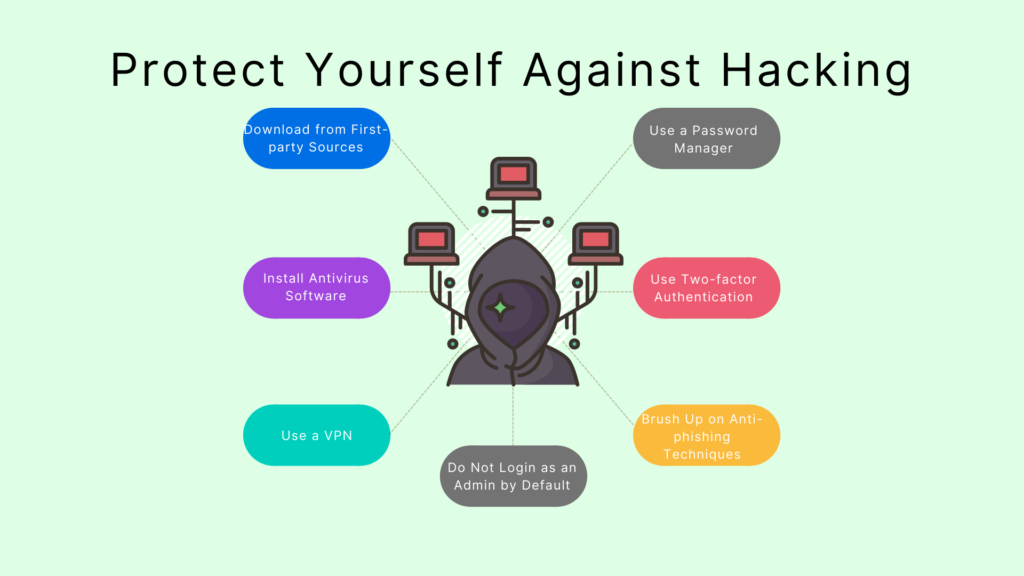
Download from First-party Sources
Only download apps and software from reputable companies and first-party websites. When users download stuff from unknown sites, they have no idea what they’re getting, and the software could be infested with malware, viruses, or Trojans.
Install Antivirus Software
Antivirus software is essential for detecting potentially dangerous files, activity, and bad actors on machines. A reliable antivirus program safeguards people and companies from the newest malware, spyware, and viruses by employing advanced detection engines to detect and block new and growing threats.
Use a VPN
Using a virtual private network (VPN) allows users to browse the internet securely. It hides their location and prevents hackers from intercepting their data or browsing activity.
Do Not Login as an Admin by Default
Hackers target firms using usernames like “admin,” which is one of the most often utilized by IT departments. Do not log in with this name by default because it makes you a hacking target. Users can browse the internet safely by using a virtual private network (VPN). It conceals their location and protects their data and surfing activities from hackers.
Use a Password Manager
It is a security best practice to create strong, unique passwords, but remembering them is challenging. Password managers are helpful tools that allow consumers to create secure, difficult-to-crack passwords without having to remember them.
Use Two-factor Authentication
Two-factor authentication (2FA) eliminates the need for passwords and ensures that the person accessing an account is who they say they are. When a person signs into their account, they are asked to give further identity proof, such as their fingerprint or a code texted to their smartphone.
Brush Up on Anti-phishing Techniques
Users must be aware of the methods used by hackers to target them. This is especially true with antiphishing and ransomware, which assist consumers in recognizing the telltale indicators of phishing emails, ransomware attacks, and ransomware settlements.
Is hacking illegal?
Hacking is acceptable in and of itself. However, hacking without permission crosses the threshold from a lawful hobby to illegal cybercrime. That’s why what white hat hackers do is legal – their companies and clients have granted them permission to hack — and why grey hat hackers could face legal consequences if they report their findings.
Of course, all black hat hacking is prohibited. If you’ve been the victim of black hat hacking, you can and should report the crime to the appropriate authorities in your nation or region. This could potentially mitigate the damage done, assist in the prosecution of the hacker, and prevent future victims.
Conclusion
Hacking is the process of detecting and exploiting flaws in computer systems and/or networks. Committing a crime using computers and information technology infrastructure is known as cybercrime. Ethical hacking is concerned with enhancing the security of computer systems and/or networks. Hacking that is ethical is legal.
Disclaimer
This article is demonstrated for instructional purposes only. It is illegal to use it in the wrong way. We don’t approve of any type of hacking in any way. End-users should be solely responsible for their own behavior.
People May Ask
Q- What is the most significant hack ever?
A- The data leak against Yahoo! is estimated to be the greatest hack in history. The business claimed that every Yahoo! client was affected by the 2013 assault, which compromised about 3 billion people.
Q- Which country has the most number of hackers?
A- China is thought to have the biggest concentration of dangerous hackers. China is responsible for the majority of serious cyberattacks around the world.
Q- What are some hacking examples?
A- Financial gain, personal data theft, access to secret information, the desire to shut down websites, as well as idealism and political activism, are all examples. While some types of hacking are perfectly lawful, the majority are not and are considered crimes.
Q- Is hacking simple?
A- Without knowing how to program, it is feasible to learn how to hack. Learning programming, on the other hand, will make it much easier for you to succeed. Almost all hacking tactics necessitate programming knowledge. If you’re a beginner, you should be aware that each programming language has advantages and disadvantages.
Q- Is hacking a profession?
A- Ethical hacking is a popular ability that can lead to a variety of interesting jobs. Some ethical hacking jobs exist to assist businesses with their digital security. Others entail obtaining evidence from crime scenes or analyzing stolen information.